CAS systems solutions has the key to help toughen your cyber defenses.

CAS systems solutions has the key to help toughen your cyber defenses. Our cyber security solutions protect your operational networks (OT), controllers (DCS, PLC, HMI, SCADA) and software systems from not only the known attack vectors, but the zero day too. We can offer a range of specialist products to help secure your systems.Our solutions are based on Defense-in-Depth Architecture usually with at least three zones, incorporating a DMZ, intrusion detection, use of firewalls, effective security policies, training programs and incident response mechanisms. Where possible OPC UA protocol is used for data aggregation and client-server communication. We provide solutions for securing systems with any combination of standard or proprietary industrial automation communication protocols.
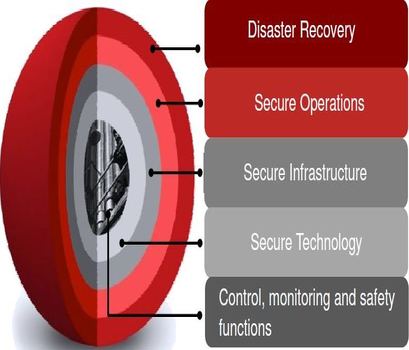
DEFENSE IN DEPTH
Our strategies delay an attacker by increasing resilience of the infrastructure against an attack to allow time for detection and response. We ensure that the time to breach the protection is greater than the combined time required to detect and respond to the event. Multiple layers of defense (Demilitarized zone, Network segmentation); Multiple layers of security controls (Anti-virus (blacklisting), Application whitelisting); Detection and response by monitoring changes in risk, security events, and Honeypot. Our Layered Approach to security includes Secure Technology (ISASecure EDSA certification for embedded devices, ISASecure SSA certification for control systems, and ISASecure SDLA certification for the development lifecycle); Secure Infrastructure (Standards and best practices such as IEC62443 (ISA99)); Secure Operations and Disaster Recovery (Standards and best practices such as NIST 800-34.
.
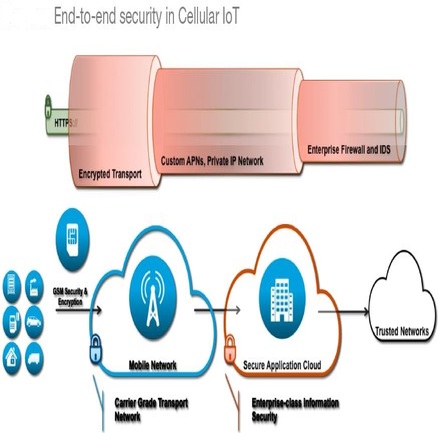
END-T0-END SECURITY
Asymmetric and Symmetric cryptography algorithms can be implemented to secure SCADA communication protocols such as Distributed Network Protocol (DNP3). Cryptography algorithms such as AES and RSA can be deployed to secure the SCADA/DNP3 communication, against authentication and confidentiality attacks and SHA-2 hashing algorithm used against integrity attacks. Digital signature which is based on hashing (using SHA-2) and RSA algorithm can be used to provide security against non-repudiation attacks.